Ransomware: record number of attacks in July, 10P to maneuver

Ransomware attacks reached an all-time high in July 2023, thanks to the exploitation of the MOVEit software by the Cl0p ransomware group.
In a new report published by the Global Threat Intelligence team of the NCC Group, analysts observe a record number of ransomware-related cyberattacks last month, with 502 major incidents identified. According to the researchers, this represents an increase of 154% year on year, compared to the 198 attacks recorded in July 2022.
The July figures represent an increase of 16% compared to the previous month, with 434 ransomware incidents recorded in June 2023.
According to NCC Group, this record number is due, in large part, to the activities of Cl0P, a notorious group linked to the exploitation of the MOVEit software.
Who is Cl0p?
Cl0p, also known or associated with Lace Tempest, is responsible for 171 of the 502 attacks of the month of July, a large number of which would be due to the exploitation of the MOVEit file transfer software.
Cl0p has been around since 2019 and is known as a Ransomware-as-a-Service (RaaS) offered to cybercriminals. Also known as TA505 — or associated with it –, Cl0p attacks high-value targets with the aim of ransoming them. Hackers often steal information before encryption via a double extortion tactic.
If the victims refuse to pay, they risk having their stolen data published online.
The MOVEit Feat
Described as a “slow-moving disaster”, the MOVEit exploit affected hundreds of organizations around the world, and data belonging to millions of people was stolen.
In May, Progress Software reported a “zero-day” vulnerability in the file transfer service, MOVEit Transfer and MOVEit Cloud, which could allow unauthorized access to customer environments. The problem is that MOVEit is used by customers whose data is critical, both directly and through software supply chains.
Among the alleged victims are the US Department of Energy, Shell, the BBC, Ofcom, the National Student Clearinghouse and many universities.
Sectors of activity concerned
In total, industrial players represent 31% of ransomware attacks, or 155 recorded incidents.
According to the researchers, professional and commercial services were the most targeted in July, with the Cl0p, LockBit 3.0 and 8Base ransomware gangs responsible for 48% of all recorded cyberattacks.
If these sectors have suffered the largest number of ransomware attacks since the beginning of the year, the consumer goods sector comes in second place, with 79 attacks, or 16% of all attacks in July.
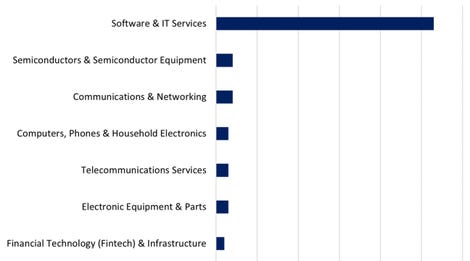
As for technology, which occupies the third place with 72 cases, or 14% of monthly attacks, NCC Group indicates that this sector “has experienced the greatest increase in absolute figures among the first three sectors this month, which is probably due to the activity of Cl0p”.
Cl0p has been responsible for 39 cyberattacks against the sector, or 54%, and this includes attacks on organizations offering IT and software services, semiconductor suppliers, electronic products and telecommunications services.
New ransomware groups are emerging
After Cl0p, Lockbit 3.0 was ranked as the second most active ransomware gang in July, responsible for 50 attacks, or 10%. Although this represents a decrease of 17% month on month, the month of July was also a field of action for the new actors of the threat and those who have changed their names, who have made their presence known.
For example, Noescape – which is believed to be a new brand of Avaddon, which closed after sending thousands of decryption keys to a media outlet in 2021 – was at the origin of 16 of the recorded attacks, joining other players such as 8Base, BianLian, BlackCat, Play and Cactus.
“Many organizations are still dealing with the impact of the Cl0p MOVEit attack, which shows how far-reaching and long-lasting ransomware attacks can be – no organization or individual is immune,” comments Matt Hull, from the NCC Group. “This campaign is all the more important because Cl0p has managed to extort hundreds of organizations by compromising a single environment. Not only should you be vigilant in protecting your own environment, but you should also pay special attention to the security protocols of the organizations with which you work as part of your supply chain.”
To go further on the ransomware wave powered by Cl0p
Source: “ZDNet.com “








