New to Linux? Here are 7 things you can do to secure your system


Picture: Richard McManus/Getty Images.
Everyone knows: Linux is much more secure than Windows. From the outset, it has been designed to be highly secure.
By installing a Linux distribution, you therefore already benefit from increased security for your use and your data. However, don’t be content with it: if a device is connected to a network, it is vulnerable.
So here are some simple tips to follow, even if you are a novice, to strengthen your security on Linux. I promise, you won’t have to edit init scripts, run commands iptables complicated or to install software like fail2ban. Rather, these are behaviors to adopt to avoid malware, ransomware and other cyberattacks.
If you are a Linux administrator, you can also share these tips with those who use it on a daily basis.
1. Make regular updates
Regardless of the operating system, this advice is always among the first to be followed. Yet many people still don’t know it.
Indeed, updates do not only bring new features or visual novelties. They mainly contain security patches to correct the vulnerabilities that have been discovered. For my part, I check for updates daily, and install them as soon as they are available. Sometimes they are minor, but other times they fix critical Common Vulnerabilities and Exposures (CVE) security vulnerabilities.
Regardless of your Linux distribution, therefore, check regularly (if you can, on a daily basis, if not on a weekly basis) if updates are available and apply them. At the end of the process, you may have to restart your computer.
2. Do not install applications from unknown sources
As on Android, the best thing to do in terms of security is to install applications only from the integrated package managers. Whether your system uses apt, dnf, snap, flatpak, pacman or zypper, it is strongly recommended to install applications only using these methods. Of course, this deprives you of many applications. But when it comes to software installation, the main motto is “prevention is better than cure”.
Nevertheless, if you find an application that you really want to install and that is not in the standard repositories, check if it is available in the form of a Snap or Flatpak package. If so, install it with one of these methods. If this is not the case and you seriously need it, do some research to verify that the repository in question is trustworthy.
Installing a single malicious application can compromise an entire system. Caution is required to prevent this situation which can turn out to be catastrophic.
3. Use a secure password
You may be thinking that this is your office, and not a server. That’s true, but that’s not a reason to use a user password like password or 12345678.
When setting your password, have two things in mind: the risks of attacks from your network and prying eyes. On your desktop computer, the most likely threat is still that someone will log in to your session and access your data. But that’s not why it can’t be as vulnerable to an intrusion by a cybercriminal who has infiltrated your network.
That is why the use of a secure and one-time password is essential. Keep in mind that this password is not only used to log in: it is also necessary to launch updates, install applications and perform admin tasks.
4. Don’t use Chrome
Most Linux distributions offer Firefox or Chromium by default to access the internet. And if Chrome, the most used web browser on the planet, can easily be installed on your OS, note that it is among the least secure browsers.
To help you make your choice, you can consult our selection of the most secure browsers. You will find Brave, Firefox, Tor, DuckDuckGo and Mullvad, but Chrome is of course not included.
If you still don’t know which one to choose for Linux, I recommend Firefox or Tor.
5. Activate your firewall
Some Linux distributions are shipped without the firewall being activated. For example, on most Ubuntu-based ones, the UFW firewall is not enabled by default. Moreover, most of them also do not offer a graphical interface for the firewall.
If you don’t want to have to execute commands (even if to activate the UFW, just run the command line sudo ufw enable), you can use the GUI gufw application. The latter can be installed from the application store of your distribution. Once you have installed it, you can activate the firewall by placing the cursor on the position We.
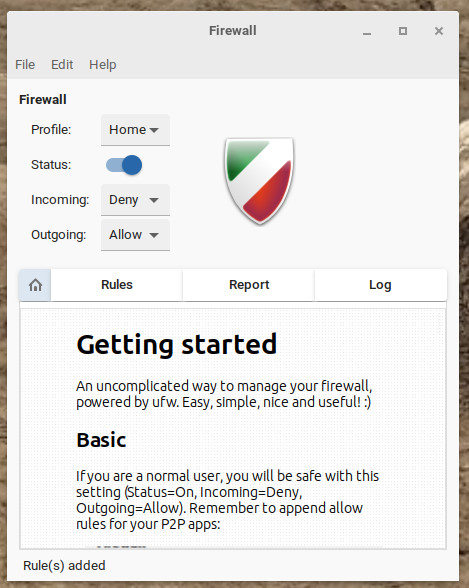
Gufw is one of the easiest to use firewall graphical interfaces. Picture: Jack Wallen/ZDNET.
Once you have activated the firewall, you can launch any service (such as SSH or Samba) that you need to authorize without having to issue commands (such as sudo ufw allow ssh).
6. Never log in as the root user
The root profile is disabled on Ubuntu distributions. Nevertheless, it is possible on other distributions (especially Debian and Fedora) to easily log in as the root user so that you can do everything without having to worry about sudo.
However, using this profile is not recommended. As a root user, you have hyper-privileged access and, if someone breaks into your system, that person will also have unlimited access to all the services, all the applications and all the data that you have stored.
So my advice is to NEVER log in as the root user. Always use sudo for admin tasks so as not to expose your system to potentially serious attacks.
7. Fully encrypt your disk
If you have installed Linux yourself on your machine and your distribution offers Full Disk Encryption (FDE), you should use it.
Why choose this solution? Suppose someone steals your laptop. If your disk is not encrypted, the person who has taken possession of your device can remove the disk, mount it on another machine (to avoid having to enter the user password) and seize the data it contains. If, on the other hand, you have activated full disk encryption, the person in possession of your computer will not be able to access your disk, unless they know the encryption password.
Of course, it is impossible to guarantee 100% that no one will be able to take over your data. After all, as the old saying goes: “when you want, you can”. But with this feature enabled, you make it much more difficult for those who will try.
Source: ZDNet.com








